Retrieval Augmented Generation (RAG) is a sophisticated approach developed to mitigate the issue of AI hallucinations. Unlike standard AI queries, RAG enhances the reliability of AI responses through a two-step process
Monthly Archives: June 2024
Cybersecurity threats have evolved significantly over the past few decades, adapting to technological advancements and changes in the digital landscape. Understanding this evolution is crucial for businesses aiming to protect their digital assets effectively. From the early days of simple viruses to today’s sophisticated, multi-vector attacks, the nature of cyber threats continues to grow in complexity
secure payment processing is crucial for businesses of all sizes. Ensuring the safety of transactions not only protects your customers but also helps maintain your business’s reputation and compliance with regulations. As cyber threats continue to evolve, implementing robust payment security measures is essential
In recent cyber security developments, experts have issued a warning to users of Google Chrome, Microsoft Word, and OneDrive. A newly uncovered cyberattack employs fake software error messages to deceive users into installing malicious software. This attack, which has been meticulously detailed by Proofpoint, a renowned cybersecurity firm, highlights the evolving tactics of hackers in their quest to steal private digital data, including cryptocurrencies like Bitcoin.
cybersecurity insurance, a crucial component of a robust cybersecurity strategy. Cybersecurity insurance helps businesses mitigate the financial risks associated with cyberattacks, providing coverage for various expenses related to data breaches, ransomware attacks, and other cyber incidents.
cybersecurity and business continuity planning (BCP) are inseparable elements crucial to maintaining operational resilience and safeguarding against disruptions. While cybersecurity focuses on protecting digital assets from threats, business continuity planning ensures that a business can continue to operate in the face of various challenges, including cyber attacks. The interplay between these two areas is vital for comprehensive risk management
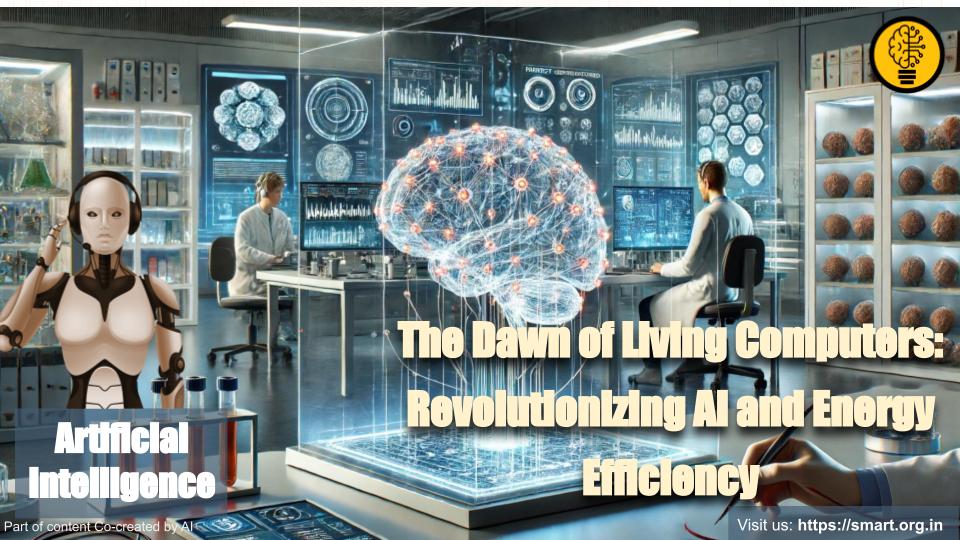
In a groundbreaking advancement that merges biology and technology, Swedish scientists have unveiled the world’s first “living computer” composed of human brain tissue.
we at Smart Group India extend our heartfelt greetings and best wishes to you and your loved ones. This auspicious occasion, also known as the “Festival of Sacrifice,” holds immense significance in the Islamic calendar and is a time for reflection, gratitude, and generosity.
As projects scale, the complexity of testing grows exponentially. Manual testing, while valuable, struggles to keep up. We’ll delve into a real-world example of how automated testing revolutionized a large project, and how a company like Smart Group India can guide you through the automation landscape.
Conducting a Cybersecurity Risk Assessment (CRA) is crucial for identifying vulnerabilities and implementing measures to protect your business’s data and systems. A well-executed risk assessment helps prioritize security efforts, ensures regulatory compliance, and mitigates potential damages from cyber incidents
- 1
- 2