The AI Revolution: Convenience at a Cost In 2025, AI is everywhere. From personalized recommendations on Netflix to AI-driven chatbots and virtual assistants, technology is making our lives easier than ever before. But here’s the catch—this convenience comes at a cost: your data. Every time you use an AI-powered service, you’re feeding it valuable personal […]
Tag Archives: digital technologies
Digital Technologies: Digital technologies encompass a wide range of electronic tools, systems, devices, and resources that generate, store, or process data. These include social media, online games, multimedia, and mobile phones. Digital technologies are integral to modern life, influencing various aspects.
Securing E-commerce platform against cyber threats is crucial to protect your business and maintain customer trust. Smart Group India, a leading cybersecurity consultancy, offers specialized services to help startups and corporates implement robust cloud security measures, ensuring the safety of their digital assets
Cybersecurity threats have evolved significantly over the past few decades, adapting to technological advancements and changes in the digital landscape. Understanding this evolution is crucial for businesses aiming to protect their digital assets effectively. From the early days of simple viruses to today’s sophisticated, multi-vector attacks, the nature of cyber threats continues to grow in complexity
secure payment processing is crucial for businesses of all sizes. Ensuring the safety of transactions not only protects your customers but also helps maintain your business’s reputation and compliance with regulations. As cyber threats continue to evolve, implementing robust payment security measures is essential
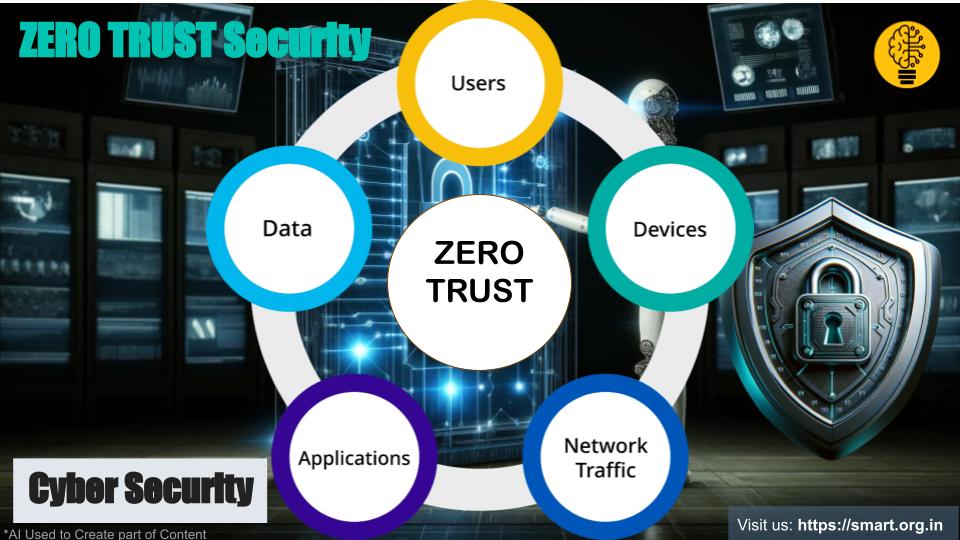
In the ever-evolving world of cybersecurity, the Zero Trust Security model has emerged as a critical strategy for businesses aiming to protect their digital assets. Unlike traditional security models that rely heavily on perimeter defences, Zero Trust assumes that threats can come from anywhere, both inside and outside the network.
The General Data Protection Regulation (GDPR), implemented on May 25, 2018, has fundamentally reshaped the landscape of data privacy in Europe and beyond. This regulation affects any business, anywhere in the world, that processes the personal data of EU citizens.
Smart Group India, a leader in cybersecurity consultancy, offers specialized services to implement Pen test for startups and corporates, ensuring their systems are robust and secure. Here’s an introduction to penetration testing and its manifold benefits.
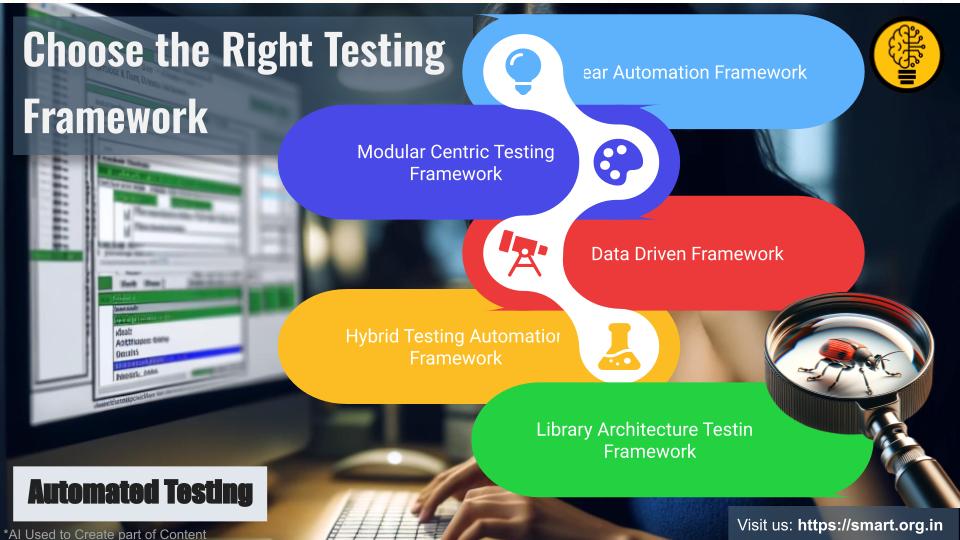
Choosing the right testing framework is crucial for the success of any software project. Whether you are a CTO, CIO, project manager, or entrepreneur, the decision impacts the quality, efficiency, and overall success of your project.
The integration of Artificial Intelligence (AI) into healthcare is revolutionizing the medical landscape. From predictive diagnostics to personalized medicine and robotic surgeries. AI’s potential to enhance patient outcomes while reducing healthcare costs is significant.
we explore the importance of education and workforce development in closing the AI skills gap. We also highlight how organizations like Smart Group India are pivotal in equipping startups with the necessary AI skills.