In the ever-evolving world of cybersecurity, the Zero Trust Security (ZTS) model has emerged as a critical strategy for businesses aiming to protect their digital assets. Unlike traditional security models that rely heavily on perimeter defences, Zero Trust assumes that threats can come from anywhere, both inside and outside the network. This proactive approach ensures robust protection against sophisticated cyber threats. Smart Group India, a leading cybersecurity consultancy, offers tailored services to help startups and corporates implement effective Zero Trust models. Here’s a comprehensive look at Zero Trust Security and its significance for modern businesses.
What is Zero Trust Security?
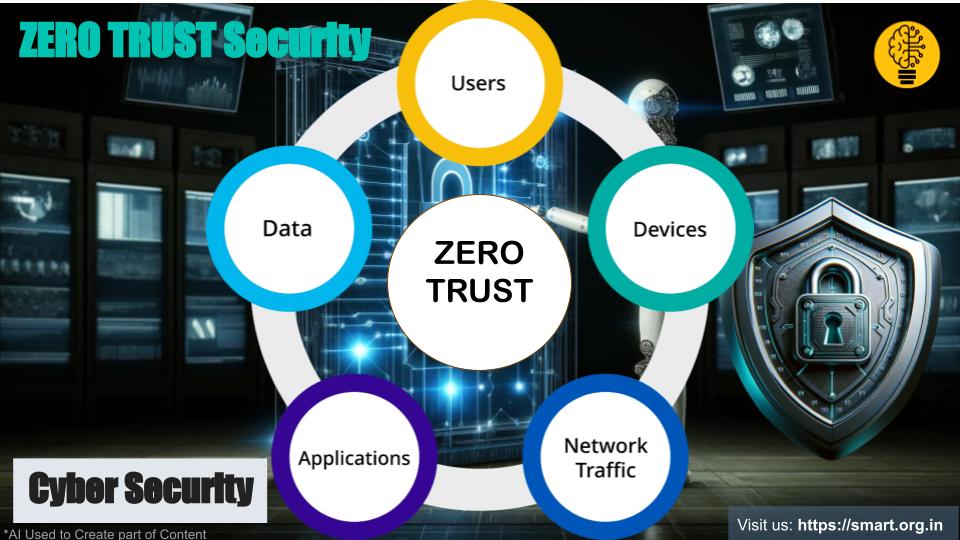
Zero Trust operates on the principle of “never trust, always verify.” This model treats every access request as potentially malicious, requiring continuous verification regardless of the request’s origin. By employing a combination of identity verification, multi-factor authentication, endpoint security, and continuous monitoring, Zero Trust ensures comprehensive security.
Core Principles of ZTS
Verify Every Identity
- Strict Authentication: Every user and device must undergo rigorous identity verification before accessing resources.
- Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security, requiring multiple forms of identification.
Enforce Least Privilege Access
- Access Controls: Users and devices receive only the minimum access necessary for their functions.
- Dynamic Policies: Access policies adapt based on user behavior, location, and device health.
Segment Your Network
- Micro-Segmentation: Divide the network into smaller segments to limit lateral movement of attackers.
- Granular Control: Apply fine-grained access controls to each segment, ensuring only authorized access.
Continuous Monitoring and Validation
- Real-Time Monitoring: Continuously monitor network traffic, user activity, and system behavior to detect anomalies.
- Behavioral Analytics: Utilize AI and machine learning to analyze user behavior and identify potential threats.
Benefits of ZTS
Enhanced Security
- Reduced Attack Surface: By not trusting any entity by default, Zero Trust significantly reduces potential entry points for attackers.
- Proactive Threat Mitigation: Continuous monitoring and real-time analytics enable early detection and response to threats.
Regulatory Compliance
- Data Protection: Ensure only authorized individuals access sensitive data, aiding compliance with regulations like GDPR and HIPAA.
- Audit Readiness: Maintain detailed logs and continuous monitoring to simplify compliance audits.
Improved User Experience
- Seamless Access: Provide secure, seamless access to resources without the need for complex VPN setups.
- Flexibility: Support secure remote access from any location, enhancing productivity and flexibility.
Implementing Zero Trust
Assess and Plan
Start by assessing your current security practices. Identify weaknesses and areas for improvement. Plan a comprehensive Zero Trust strategy that aligns with your business goals.
Develop Custom Frameworks
Create a tailored Zero Trust framework that meets your specific needs. This should include identity management, MFA, micro-segmentation, and continuous monitoring.
Integrate Necessary Technologies
Integrate the technologies required to implement your Zero Trust strategy. This includes identity verification systems, endpoint security solutions, and real-time monitoring tools.
Train and Support
Provide thorough training for employees to understand and follow Zero Trust principles. Offer ongoing support to ensure the effectiveness of security measures.
Smart Group India’s Role in Zero Trust Implementation
Smart Group India excels in offering cybersecurity consultancy services tailored to the unique needs of startups and corporates. They help businesses adopt Zero Trust Security models through:
- Customized Security Solutions: Smart Group India develops personalized Zero Trust frameworks that address specific business risks.
- Technology Integration: They assist in deploying and integrating the necessary technologies to support a Zero Trust environment.
- Continuous Support: Smart Group India provides ongoing monitoring and support, ensuring that security measures remain effective against emerging threats.
- Employee Training Programs: They offer comprehensive training to help employees understand and adhere to Zero Trust Security principles.
The Zero Trust Security model is essential for modern businesses aiming to protect their digital assets from increasingly sophisticated cyber threats. By adopting a “never trust, always verify” approach, businesses can significantly enhance their security posture. Implementing Zero Trust requires a comprehensive strategy that includes strict identity verification, least privilege access, micro-segmentation, and continuous monitoring. With Smart Group India’s expertise, businesses can effectively navigate the complexities of Zero Trust, ensuring robust protection against cyber threats and maintaining compliance with regulatory standards. In today’s digital age, Zero Trust is not just a security measure but a necessity for safeguarding business integrity and data.

In conclusion, we at Smart Group hope this article has provided you with valuable insights and actionable strategies. Smart Group India Incubation provides a nurturing environment for startups, offering comprehensive support and resources to foster growth and innovation. With access to expert mentorship, state-of-the-art infrastructure, and networking opportunities, startups can thrive in their journey from ideation to market launch. Explore our services in DevOps consultancy, IoT solutions, and cybersecurity to leverage cutting-edge technology for your business success. Join us to embark on a transformative journey towards entrepreneurial excellence. For further information and a deeper dive into this topic, we encourage you to explore the following resources. These links offer a wealth of knowledge and expert opinions that can enhance your understanding and assist you in applying these concepts effectively.
Startup Policies Govt. Of India
Startup News Sites
Publications
Research Papers