where technology is constantly evolving, keeping software up to date is crucial. Regular software updates and effective patch management are essential practices for maintaining the security and performance of your systems. Ignoring these practices can expose your business to significant risks, including cyberattacks, data breaches, and operational disruptions. This blog explores the importance of regular software updates and patch management, and highlights how Smart Group India can help businesses implement robust cybersecurity measures.
Category Archives: Cyber Security
Cybersecurity threats are rapidly evolving, with sophisticated attacks like ransomware, phishing, and data breaches becoming increasingly prevalent. The interconnected nature of digital systems has heightened vulnerabilities, making both individuals and organizations potential targets. These threats not only jeopardize sensitive data but also pose significant risks to the integrity of critical infrastructure and the overall digital economy.
The proliferation of mobile devices in the workplace has revolutionized the way businesses operate. Employees can now access corporate data and perform their duties from virtually anywhere, enhancing productivity and flexibility. However, this convenience comes with significant security risks. Mobile security, especially in the context of protecting corporate data on personal devices, is a critical concern for businesses
Securing E-commerce platform against cyber threats is crucial to protect your business and maintain customer trust. Smart Group India, a leading cybersecurity consultancy, offers specialized services to help startups and corporates implement robust cloud security measures, ensuring the safety of their digital assets
Cybersecurity threats have evolved significantly over the past few decades, adapting to technological advancements and changes in the digital landscape. Understanding this evolution is crucial for businesses aiming to protect their digital assets effectively. From the early days of simple viruses to today’s sophisticated, multi-vector attacks, the nature of cyber threats continues to grow in complexity
secure payment processing is crucial for businesses of all sizes. Ensuring the safety of transactions not only protects your customers but also helps maintain your business’s reputation and compliance with regulations. As cyber threats continue to evolve, implementing robust payment security measures is essential
cybersecurity insurance, a crucial component of a robust cybersecurity strategy. Cybersecurity insurance helps businesses mitigate the financial risks associated with cyberattacks, providing coverage for various expenses related to data breaches, ransomware attacks, and other cyber incidents.
cybersecurity and business continuity planning (BCP) are inseparable elements crucial to maintaining operational resilience and safeguarding against disruptions. While cybersecurity focuses on protecting digital assets from threats, business continuity planning ensures that a business can continue to operate in the face of various challenges, including cyber attacks. The interplay between these two areas is vital for comprehensive risk management
Conducting a Cybersecurity Risk Assessment (CRA) is crucial for identifying vulnerabilities and implementing measures to protect your business’s data and systems. A well-executed risk assessment helps prioritize security efforts, ensures regulatory compliance, and mitigates potential damages from cyber incidents
Smart Group India’s expertise in implementing Artificial Intelligence in Cybersecurity solutions ensures that startups and corporates can effectively leverage this technology to safeguard their data
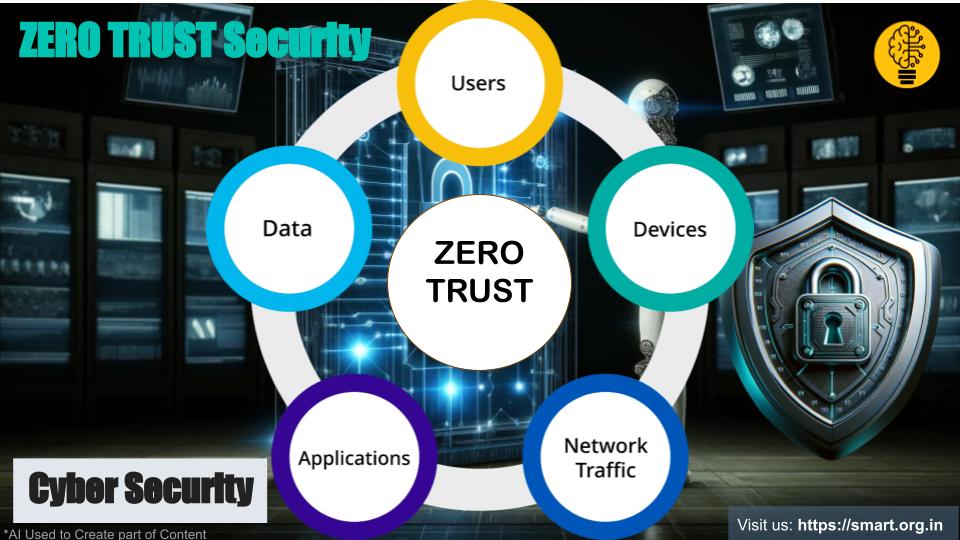
In the ever-evolving world of cybersecurity, the Zero Trust Security model has emerged as a critical strategy for businesses aiming to protect their digital assets. Unlike traditional security models that rely heavily on perimeter defences, Zero Trust assumes that threats can come from anywhere, both inside and outside the network.